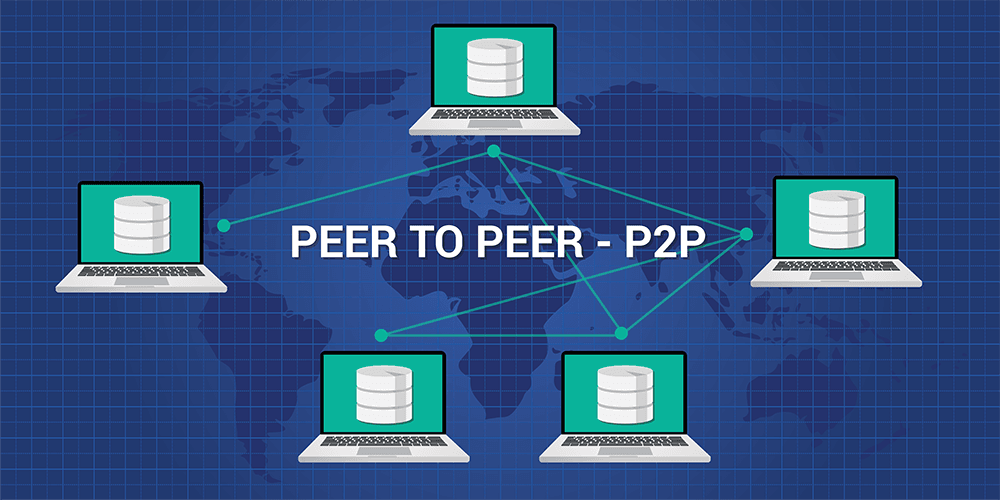
P2P IoT architectures offer a revolutionary alternative to traditional cloud-based models, enabling direct device-to-device communication for enhanced speed, security, and scalability. At dev-station.tech, Dev Station Technology believes this decentralized approach is the key to unlocking the full potential of your connected ecosystem. Explore the world of direct device interaction and decentralized networks.
Contents
ToggleWhat Are the 3 Main Advantages of a P2P IoT Architecture?
A Peer-to-Peer (P2P) IoT architecture provides three primary advantages: enhanced security and privacy by eliminating central servers, significantly reduced latency for real-time applications, and lower operational costs by minimizing cloud infrastructure and bandwidth expenses.
The Internet of Things (IoT) has traditionally relied on a centralized, cloud-based model where devices send data to a central server for processing, and commands are relayed back. While functional, this model introduces challenges related to latency, cost, and security. A Peer-to-Peer (P2P) IoT network fundamentally changes this dynamic. In a P2P model, devices can discover, connect, and communicate directly with each other without routing data through a central server, creating a more resilient and efficient system. Let’s explore the three core benefits this decentralized approach offers.
1. How Does P2P Enhance Security and Privacy?
P2P enhances security by eliminating the single point of failure and attack vector of a central server. Data is exchanged directly between authenticated devices using end-to-end encryption, and since data can be stored locally, user privacy is significantly improved as less sensitive information is held by a third-party cloud provider.
In a centralized iot architecture, the cloud server is a lucrative target for cyberattacks. A single breach can compromise the entire network and expose the data of every connected device. P2P networks mitigate this risk by distributing communication. The distributed nature of these P2P platforms makes it difficult for attackers to launch effective large-scale attacks.
Furthermore, platforms using P2P connections enable end-to-end encryption between the user’s client (like a smartphone app) and the IoT device itself. This means that even the company facilitating the connection cannot access the data stream, a crucial feature for privacy-sensitive applications like smart security cameras or medical devices. By keeping data local to the device or within the user’s private network, P2P models align better with privacy regulations like GDPR, as there is no third-party server storing personal data.
2. How Does P2P Reduce Latency and Improve Performance?
P2P communication drastically reduces latency by creating a direct path for data between devices, eliminating the round-trip delay to a distant cloud server. This is critical for time-sensitive applications requiring real-time control and responsiveness, such as remote machinery operation or smart home interactions.
Consider the remote control of a smart security camera. In a cloud-based system, the command from your phone travels to a server, which then relays it to the camera. This entire process can introduce delays of several seconds. Research shows that a response time above 0.1 seconds feels unnatural to users. A P2P connection, however, allows your phone to communicate directly with the camera, making controls like panning or zooming feel instantaneous.
This low-latency advantage is a game-changer for industrial IoT (IIoT) and vehicle-to-vehicle (V2V) communication, where split-second decisions are essential for safety and efficiency. By processing data closer to the source, a concept aligned with edge computing, P2P networks ensure that critical actions are not delayed by network congestion or cloud server processing queues.
3. How Can P2P Architectures Lower IoT Operational Costs?
P2P architectures significantly lower costs by reducing reliance on expensive central cloud servers for data relay and storage. This model decreases bandwidth consumption, minimizes or eliminates cloud subscription fees, and simplifies the overall infrastructure, leading to a much lower total cost of ownership.
In a standard cloud IoT setup, every piece of data from every device is sent to the cloud. This incurs costs for data ingestion, processing, and storage. As the number of devices scales into the thousands or millions, these costs can become substantial.
A P2P model avoids this constant data flow. For example, in a smart home, a motion sensor can directly tell a light to turn on without ever sending a packet to the cloud. This not only reduces bandwidth costs but also eliminates the need for a powerful cloud application to process these simple interactions. Some P2P IoT platform providers note that their infrastructure costs are much lower because they only mediate connections rather than processing all the data. This leaner approach makes the solution more cost-efficient and easier for developers to manage, as they can focus on the client and device applications instead of complex cloud backend development.
How Does a P2P IoT Network Compare to a Centralized Model?
A P2P IoT network is a decentralized system where devices communicate directly, offering high resilience and low latency. In contrast, a centralized model relies on a central cloud server to mediate all communication, which creates a single point of failure and can introduce significant delays and costs.
To understand the difference, it’s helpful to compare key architectural characteristics. The four primary systems of any IoT technology are devices/sensors, connectivity, data processing, and user interface. The main difference between P2P and centralized models lies in how connectivity and data processing are handled.
| Characteristic | P2P IoT Architecture | Centralized (Cloud) IoT Architecture |
|---|---|---|
| Data Path | Device ↔ Device (Direct) | Device → Cloud → Device |
| Single Point of Failure | No, the network is resilient. | Yes, the central server. |
| Latency | Very Low | Higher, dependent on server distance. |
| Scalability | High, as network capacity grows with each new device. | Depends on server capacity, can be expensive. |
| Infrastructure Cost | Low, minimal server requirements. | High, requires powerful cloud infrastructure. |
This structure of distributed systems in P2P IoT not only improves resilience but also fosters a more democratic and autonomous network where devices can collaborate without a central authority dictating their interactions.
Which Platforms and Frameworks Support P2P IoT?
Several platforms specialize in or support P2P IoT, including IOTA, which uses a decentralized ledger called Tangle; Nabto, which focuses on secure P2P connectivity for remote control; and Helium, which provides a decentralized wireless network. Other technologies like blockchain can also serve as a foundation for P2P IoT applications.
For developers and researchers looking for P2P IoT platforms, the landscape is growing. These platforms provide the necessary tools and infrastructure to build and deploy decentralized IoT solutions. Here are a few notable examples:
- IOTA: This platform uses a unique architecture called Tangle, which is a Directed Acyclic Graph (DAG) that allows for fee-less, secure data and value exchange between devices. It is specifically designed for the machine-to-machine economy.
- Nabto: The Nabto platform is built specifically for creating direct, secure P2P connections between an end-user client (like a mobile app) and an IoT device. It is widely used for applications where low latency is critical, such as smart cameras and remote access to machinery.
- Helium: Helium has created a decentralized, global wireless network for IoT devices. Individuals can host hotspots and are rewarded in cryptocurrency, creating a P2P network for long-range, low-power device connectivity.
- Filament: This platform uses a decentralized ledger and its Blocklet technology to enable autonomous and secure communication between IoT devices, particularly for industrial applications.
Choosing the right platform depends on your specific use case, whether you need value exchange (IOTA), low-latency remote control (Nabto), or wide-area network coverage (Helium). At Dev Station Technology, we can help you navigate these options.
How Can You Implement a P2P IoT Network?
Implementing a P2P IoT network involves several key steps: selecting an appropriate communication protocol (like MQTT or CoAP over P2P), ensuring a robust device discovery mechanism, implementing strong security protocols for authentication and encryption, and developing the logic for direct device-to-device interaction.
While the specifics vary based on the chosen platform and technology, here is a general, step-by-step guide for developers looking to implement a P2P IoT solution.
- Step 1: Define Requirements and Choose a Protocol
First, clearly define your application’s needs. Does it require real-time data? Is it battery-powered? Based on this, select a communication protocol. While protocols like MQTT and CoAP are traditionally client-server, they can be used in P2P-like scenarios with local brokers or through specific P2P platforms. Technologies like Bluetooth Low Energy (BLE) or Wi-Fi Direct are inherently suited for direct, local P2P communication. - Step 2: Implement Device Discovery
Devices need a way to find each other on the network to communicate. This can be achieved through broadcasting their presence over Wi-Fi or Bluetooth, or by using more advanced methods like a Distributed Hash Table (DHT) for larger, more complex networks. The goal is to allow a new device to join the network and establish connections with its peers autonomously. - Step 3: Establish Secure Connections
Security is paramount. Since there’s no central authority, security mechanisms must be distributed. Implement end-to-end encryption for all data transmissions. Use robust authentication methods, such as public key cryptography, to ensure that devices are only communicating with trusted peers and prevent malicious nodes from joining the network. - Step 4: Develop the P2P Communication Logic
Write the application logic that handles the direct data exchange. This involves programming how devices share resources, distribute tasks, and make collaborative decisions. For example, in a smart home, you would program the motion sensor to send a message directly to the smart bulb’s IP address on the local network. - Step 5: Test and Deploy
Thoroughly test the network’s resilience. What happens if one device goes offline? Does the network reconfigure itself? Test the security protocols against potential attacks. Once you are confident in the system’s robustness, you can proceed with deployment.
For a more detailed technical consultation on building your own P2P IoT platform, you can contact the experts at Dev Station Technology.
Ready to Build a More Secure and Efficient IoT Solution?
Peer-to-peer architecture is the future of IoT. Let Dev Station Technology guide you in leveraging this powerful approach for your next project.
Learn more about our advanced IoT solutions at dev-station.tech or contact our team directly for a consultation at sale@dev-station.tech.