Modern products need software, silicon, and safety to work together. This guide shows how embedded systems go from idea to launch. It covers the whole process, from start to finish, to keep products reliable.
Embedded software runs on special hardware with strict limits. It must react fast, keep data safe, and pass audits. These rules guide every step, from planning to launch.
The process is strict and measurable. Teams use co-design, early risk control, and constant checks to reduce errors. Dev Station Technology offers expertise in embedded engineering, including ARM Cortex-M, ARM Cortex-A, and RISC-V.
Readers will learn how to set clear goals, choose the right hardware and software, and design a strong system. They will also see how to test and validate products. This includes unit tests, integration tests, and checks for safety and security.
This guide is for anyone making medical devices, industrial controllers, or connected products. It offers practical steps and decisions for teams in the United States, the UK, and Australia.
Contents
ToggleKey Takeaways
- A disciplined embedded lifecycle links concept, engineering, and compliance to business outcomes.
- Constraints in real-time systems drive choices in system architecture and firmware development.
- Hardware–software co-design reduces risk and shortens schedules.
- Early requirements and platform selection set the pace for product development.
- Continuous verification and standards alignment improve safety, security, and reliability.
- Dev Station Technology offers proven embedded engineering across MCUs, MPUs, RTOS, and connectivity.
What Is Embedded Software and How It Powers Modern Devices
In everyday products, like cars and hospital equipment, tiny computers run focused code. This code is made to manage sensors, actuators, and connectivity under strict limits. At Dev Station Technology, we focus on delivering reliable behavior in the field.
Understanding firmware vs software helps us judge risk and scope. Firmware is close to the silicon and boot flow. Higher-level software adds apps or services. The right balance depends on constraints, a real-time operating system choice, and whether the platform favors MCU vs MPU.
Defining embedded systems versus general-purpose computing
General-purpose machines run many apps and accept variable loads. Embedded devices execute fixed tasks with deterministic timing and low energy use. They often ship without a screen, emphasize reliability, and apply a real-time operating system or bare-metal loop for tight control.
This embedded software definition also clarifies firmware vs software boundaries: bootloaders, drivers, and board support packages sit near hardware, while control logic and services sit above them. Choices like MCU vs MPU shape how memory protection, latency, and cost play out.
Real-world examples across automotive, IoT, medical, and industrial
Automotive ECUs coordinate fuel, braking, ADAS, and battery health over CAN, LIN, and Automotive Ethernet. ISO 26262 drives safety-critical software practices and tool checks at scale.
IoT systems span smart thermostats, wearables, and home hubs using Bluetooth Low Energy, Wi‑Fi, Thread, Matter, and Zigbee with MQTT or HTTP backends. Here, firmware vs software choices guide update size, boot security, and radio duty cycles.
Medical platforms such as infusion pumps and patient monitors follow IEC 62304 with ISO 14971 risk controls. Industrial controllers—PLCs, motor drives, and robots—connect via Modbus, PROFINET, EtherCAT, or OPC UA, often aligned to IEC 61508 for functional safety.
Key constraints: memory, power, real-time deadlines, and safety
Many MCUs ship with tight RAM and flash, pushing efficient C/C++ and careful buffer design. Power budgets demand sleep states, clock gating, and tuned sensor sampling. Meeting deadlines means bounded latency, priority-aware ISRs, and a real-time operating system with predictable scheduling.
For safety-critical software, engineers add watchdogs, brown-out detection, ECC memory, and defined fail-safe states. These measures reduce fault impact while keeping throughput and responsiveness within target levels.
Hardware-software co-design and its impact on architecture
Hardware-software co-design aligns silicon, board layout, and code from the start. Peripheral choices—ADC, DMA, timers—must match throughput and jitter needs. Teams assess MCU vs MPU to decide on isolation, MMU use, and cost versus performance.
Architecture follows from these calls: bare-metal loops for tiny footprints, a real-time operating system for multitasking control, or Linux on an MPU for rich apps. Secure boot, driver stacks, and A/B OTA strategies complete the path from concept to resilient deployment across embedded devices and IoT systems.
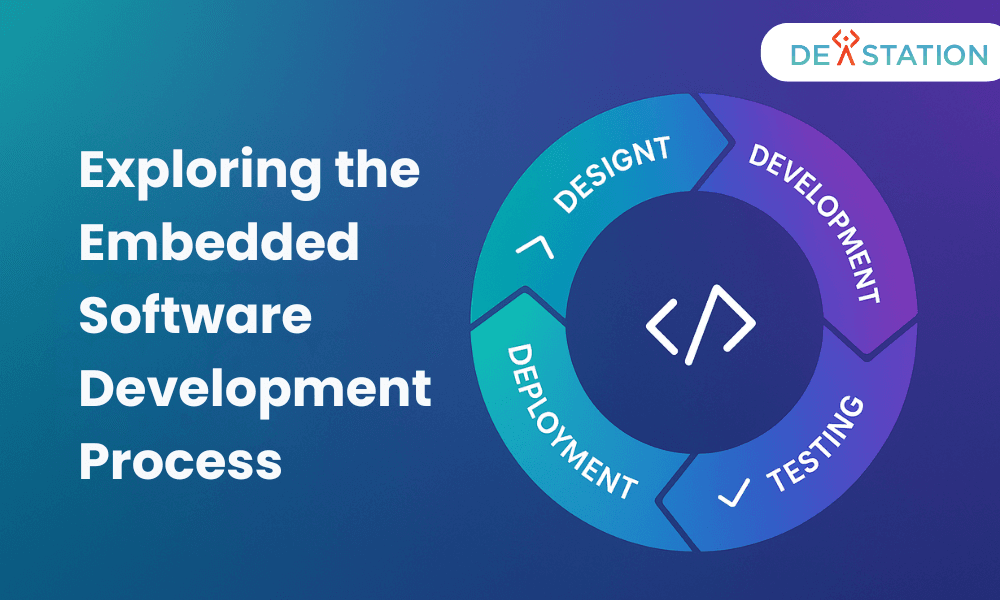
embedded software development process
The embedded software lifecycle has a clear path that balances rigor and speed. Dev Station Technology uses the V-model for safety, and Agile for embedded for quick feature updates. A light stage-gate ensures decisions at key points.
Concept and feasibility check if the market fits and if it’s technically possible. Teams set success criteria, a risk register, and a basic architecture. Early decisions guide requirements traceability and change control.
Requirements engineering turns goals into detailed items with clear criteria. IDs are tracked in a matrix, linking tests and commits to goals.
System architecture and co-design divides tasks into hardware, firmware, and cloud parts. It sets up interfaces, memory, timing, and power targets before coding starts.
Detailed design outlines modules, tasks, and error paths. It includes designs for bootloaders, updates, and diagnostics. These plans link to the matrix for traceability and audits.
Implementation follows strict coding rules with reviews and analysis. Teams use RTOS or Linux for tasks and queues. DevOps for firmware offers quick feedback through pipelines.
Integration involves setting up the board, drivers, and middleware stacks. Feature toggles allow safe introduction of new features.
Verification and validation include unit, integration, and system tests. These tests run in CI/CD pipelines on hardware farms.
Compliance and certification gather evidence for standards like ISO 26262. The V-model ensures all tests are ready for audits.
Release and manufacturing prepare for production, tests, and updates. stage-gate reviews check readiness and enforce control.
Operations and maintenance use OTA pipelines and observability. Updates follow strict rules in Jira, GitHub, or Azure DevOps.
Hybrid delivery works well here. Agile for embedded drives sprints, while the V-model anchors verification. DevOps and CI/CD pipelines ensure quality. Strong traceability and control keep risks low and teams aligned.
- Outcomes include predictable delivery and lower defect density through automated checks.
- Auditable builds and artifacts accelerate reviews and certifications.
- Faster iterations arrive from tight feedback loops on real hardware.
Planning and Requirements Engineering for Reliable Systems
Dev Station Technology starts every project with clear requirements engineering and a detailed system specification. The goal is to make decisions early that work under stress, audits, and updates. Here’s how to create software that meets expectations and grows with needs.

Translating product goals into measurable software requirements
Begin with what users and markets need. Then, outline system-level use cases and service life. Turn each goal into specific targets: like a 10 ms control loop, memory limits, and boot times.
Define how interfaces and messages should work. Mention SPI, I2C, and UART rates, error states, and backup plans. For each part of the system specification, add how to check it and a method to verify it later.
Safety, security, and regulatory considerations (ISO 26262, IEC 62304, DO-178C)
Plan for functional safety from the start. Map features to ISO 26262 ASIL levels and IEC 62304 processes. Use DO‑178C DAL levels or IEC 61508 for industrial control.
Protect the product with cybersecurity for embedded standards. Use STRIDE threat modeling and secure boot. Include SBOM outputs in SPDX or CycloneDX to meet U.S. and FDA rules.
Choosing MCU/MPU, RTOS, and connectivity stacks early
Decide on MCU selection early to set cost, power, and OS options. STMicroelectronics STM32, NXP Kinetis or i.MX RT, and Microchip SAM are good for low power. MPUs like NXP i.MX 6/8 or Texas Instruments Sitara support Linux and high performance.
Choose an RTOS selection based on timing and certification needs. FreeRTOS, Zephyr, ThreadX/Azure RTOS, or QNX fit different needs. Linux with PREEMPT_RT is good for soft real time. Pick connectivity stacks with security and OTA support: Bluetooth LE, Wi‑Fi, cellular LTE‑M/NB‑IoT, or Ethernet with TLS.
Risk analysis, FMEA, and traceability from requirements to tests
Do early hazard analysis and FMEA to find failure modes and their effects. Use redundancy, safe states, and diagnostics to mitigate risks. Link each risk to a mitigation and a test case for clear coverage.
Keep a live traceability matrix that connects requirements to design, code, tests, and results. Tools like Polarion, Jama Connect, or Codebeamer help with traceability and audit readiness.
Design, Implementation, and Toolchains That Accelerate Delivery
Good software architecture makes complex devices simple and easy to test. It breaks down work into tasks with clear priorities. This makes it easier to manage and predict how devices will behave.
Using HAL and drivers keeps the application code clean and easy to move between devices. It’s important to separate the bootloader, application, and secure storage. This makes it easier to find and fix problems.
RTOS design patterns help teams organize their work. They use state machines and schedules to make sure devices work well under stress. A publish/subscribe bus helps keep things simple and safe.
Quality comes from following rules and checking work carefully. Teams should use MISRA C/C++ and CERT rules. They should also test their code thoroughly using tools like Unity, CppUTest, or GoogleTest.
Using the right tools makes work faster. IAR Embedded Workbench and Keil MDK give detailed feedback and help make code smaller. GCC and Clang with CMake and Ninja make it easy to work across different platforms.
For embedded Linux, the Yocto Project makes images that are easy to understand. CMake helps build code for different platforms. This makes it easier to fit code into tight spaces.
Good debugging tools are essential. J-Link, ST-LINK, and Lauterbach TRACE32 help find timing issues. ARM CoreSight ETM and SWO ITM logs help find rare problems.
Model-based code generation makes math-based code faster and safer. MATLAB and Simulink with Embedded Coder turn models into safe code. Tools like STM32CubeMX and NXP MCUXpresso make setting up devices easier.
Modern development relies on CI/CD for embedded systems. This includes using hardware-in-the-loop rigs, emulators, and Docker images. It keeps everything versioned, signed, and easy to reproduce.

- Define tasks and queues with clear priorities and budgets.
- Use code generation for validated control paths and drivers.
- Tune compilers, analyze maps, and enforce size targets.
- Trace timing with ETM and log via SWO for fast root cause.
- Keep CI green with staged tests and deterministic builds.
| Area | Practice | Primary Tools | Outcome |
|---|---|---|---|
| Architecture | State machines, publish/subscribe, time-triggered loops | RTOS design patterns, HAL and drivers | Predictability and low coupling |
| Build and Compile | Portable builds, LTO, -Os/-O2 tuning | IAR Embedded Workbench, Keil MDK, GCC, Clang, CMake | Smaller binaries and stable performance |
| OS and Distribution | Custom images with traceable components | Yocto Project, Buildroot | Lean, auditable firmware stacks |
| Debug and Trace | On-target timing and event logging | J-Link, ST-LINK, Lauterbach TRACE32, ARM CoreSight ETM, SWO | Faster fixes for real-time issues |
| Model and Configure | Model-based workflows and device setup | MATLAB/Simulink with Embedded Coder, STM32CubeMX, NXP MCUXpresso | Reliable code generation and quicker bring-up |
| Automation | Versioned builds, HIL, emulation | CI/CD for embedded with Jenkins, GitLab CI, GitHub Actions, QEMU, Renode, Docker | Repeatable releases and tighter feedback loops |
Dev Station Technology uses these methods to make devices easy to use and maintain. This approach helps teams work better together, reduces risks, and keeps projects on track.
Verification, Validation, and Compliance in Embedded Development
Dev Station Technology views verification as a key engineering discipline. Each build is tested rigorously in the lab and in real-world settings. This ensures the code works as expected in various environments.
Unit, integration, HIL/SIL testing, and code coverage strategies
Unit tests focus on individual functions, using mocks for peripherals. Integration tests combine drivers and the application on the target board. This reveals any timing or API issues.
Software-in-the-loop tests the build on emulators or QEMU for quick edge case checks. Hardware-in-the-loop tests connect real sensors and actuators to test corner cases.
Code coverage guides the testing effort, focusing on critical areas. Tools like gcov and lcov provide fast feedback. For certification, VectorCAST and LDRA are used.
Static analysis, MISRA compliance, and code quality gates
Static analysis tools catch defects early. Coverity, Klocwork, and others flag issues like null dereferences and dead code. This saves time in the lab.
MISRA C:2012 rules ensure safe coding practices. Deviations are documented, and style is enforced. Cleanliness is checked before code is merged.
Defect tracking dashboards help spot regressions quickly. This ensures issues are caught within hours, not days.
Performance profiling, power measurement, and real-time analysis
Performance profiling is crucial for real-time systems. Tools like SEGGER SystemView measure latency and jitter. This ensures deadlines are met.
Memory checks monitor stack and heap usage. CPU load under stress helps optimize scheduling. This keeps the system running smoothly.
Power analysis uses meters and on-chip monitors. This helps manage power consumption and meet battery targets.
Security testing: threat modeling, fuzzing, and secure boot validation
Security starts with threat models. These outline assets, trust boundaries, and potential attacks. Cryptography and key storage are tested thoroughly.
Fuzz testing uses tools like AFL++ to test protocols. Long soak runs expose bugs. Interfaces are tested for security.
Secure boot is tested from start to finish. It ensures only authorized firmware runs. This includes signed images and rollback protection.
Conclusion
Embedded innovation thrives on a clear and disciplined process. Success comes from clear requirements, early platform choices, and a solid architecture. Teams that blend the V-model with Agile sprints boost reliability and speed to market.
Investing in co-design and automated testing pays off quickly. Benefits include better coverage, fewer defects, and predictable power use. These practices also help in meeting regulatory standards, keeping teams on track with user needs.
In the United States, Dev Station Technology offers comprehensive support. They help with everything from defining requirements to setting up toolchains and managing updates. Their approach ensures projects are well-managed and successful.
The key to success is clear requirements, choosing the right tools early, and following coding standards. Automation and safety and security should be part of the process from the start. By following these steps, you can improve your product’s reliability, get it to market faster, and meet compliance standards with Dev Station Technology’s help.