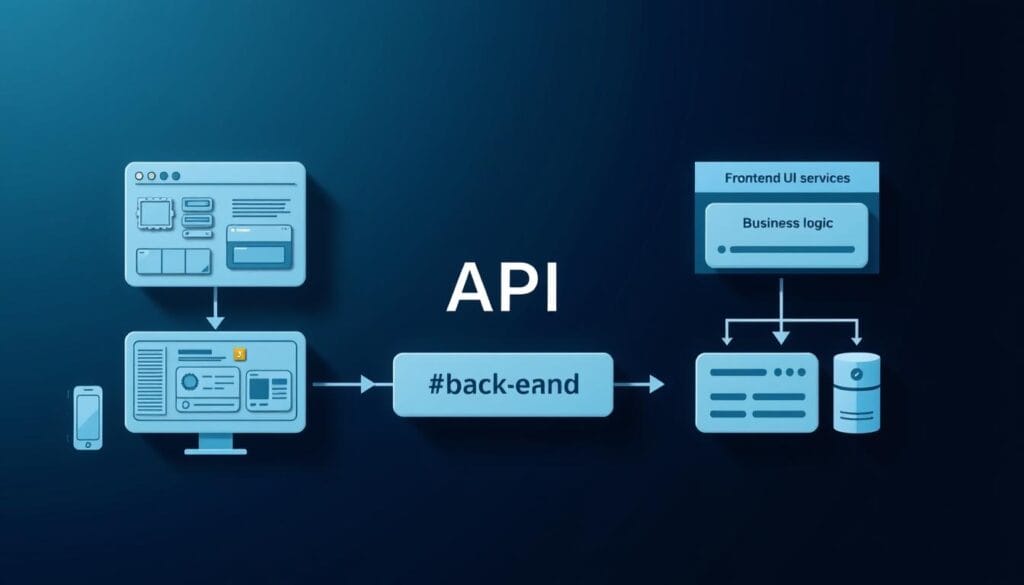
Every digital experience relies on an unseen framework that processes data, manages security, and powers functionality. This hidden architecture acts as the central hub for user interactions, ensuring smooth operations behind intuitive interfaces. For technical leaders, grasping its structure is critical for building reliable solutions that align with business goals.
Modern systems require expertise in server configuration, database optimization, and secure API design. These components work together to handle everything from user authentication to real-time analytics. Scalability remains a top priority, as platforms must adapt to growing traffic without compromising performance.
Choosing between custom-built solutions and preconfigured services depends on specific project needs. Custom setups offer tailored control, while third-party platforms accelerate deployment. Technical decision-makers must weigh factors like budget, timeline, and long-term maintenance when planning their strategy.
Contents
ToggleKey Takeaways
- Core systems manage data storage, security protocols, and integration with external tools
- Server infrastructure and API design directly impact application performance
- Scalable solutions adapt to user growth without requiring complete overhauls
- Security measures protect sensitive information across all interactions
- Technical leaders must balance customization needs with deployment timelines
- Performance monitoring ensures consistent service delivery
Understanding the Landscape of Mobile App Backends
The mobile app landscape has transformed dramatically, shifting priority from interface design to the systems powering seamless interactions. While frontend elements like buttons and screens remain visible, what users don’t see often determines success. Technical leaders now recognize that robust infrastructure drives everything from instant loading times to personalized features.
Evolution from Frontend to Backend Focus
Early mobile solutions prioritized visual appeal, but growing expectations forced a strategic pivot. Today’s users demand instant access to updated content, synchronized across devices. This requires architectures capable of handling real-time data flows and sudden traffic spikes without lag.
Modern systems now act as invisible engines, managing tasks like authentication and analytics. They ensure features work smoothly whether a user’s on Wi-Fi or cellular networks. This shift reflects market demands for reliability over superficial design trends.
Role in Enhancing Mobile User Experience
Superior performance hinges on how well hidden components process requests. Predictive analytics anticipate user needs, while intelligent caching reduces load times. These optimizations keep engagement high and frustration low.
For example, a shopping platform using advanced synchronization can update cart items across devices in milliseconds. Such responsiveness builds trust and loyalty. Technical teams must balance speed with security, ensuring data protection never slows interactions.
Key Components of a Robust Backend System
Modern digital platforms depend on synchronized technical elements working behind the scenes. Two pillars form this foundation: adaptable server structures and intelligent data handling. Together, they ensure systems scale efficiently while maintaining speed and security.
Server Infrastructure and Cloud Integration
Powerful server setups now combine physical hardware with cloud flexibility. Virtualization lets teams run multiple environments on shared machines, cutting costs without sacrificing performance. “The cloud isn’t just storage—it’s a dynamic engine for growth,” notes a Google Cloud architect.

Containerization takes this further by packaging apps with their dependencies. This prevents conflicts between versions and simplifies updates. Leading providers like AWS and Azure offer tools that automate scaling during traffic spikes.
Effective Database Management
Databases determine how quickly systems retrieve and update information. Choosing between SQL and NoSQL impacts everything from query speed to scalability. Proper indexing and replication strategies keep response times under 200ms, even during peak loads.
| Database Type | Best For | Scalability | Examples |
|---|---|---|---|
| Relational (SQL) | Structured data | Vertical | MySQL, PostgreSQL |
| NoSQL | Unstructured data | Horizontal | MongoDB, Cassandra |
| NewSQL | High-volume transactions | Hybrid | Google Spanner |
Cloud-native databases integrate seamlessly with serverless architectures. Automated backups and encryption protocols ensure data remains protected without manual oversight. This synergy allows platforms to handle millions of requests daily while staying agile.
Differentiating Frontend and Backend Development
Digital products require two distinct skill sets working in tandem: one shaping user-facing elements, the other engineering the systems that drive them. This separation ensures applications look polished while functioning reliably behind the scenes.
Visual Design Versus Underlying Functionality
Frontend specialists transform visual concepts into interactive experiences. They use HTML, CSS, and JavaScript to ensure layouts adapt seamlessly across devices—from widescreen monitors to mobile screens. Cross-browser testing guarantees buttons respond instantly, regardless of whether users access platforms through Chrome, Safari, or Firefox.
Meanwhile, server-side experts focus on data flow and logic execution. They design APIs that process requests in milliseconds and configure databases to handle millions of transactions. Security protocols like OAuth2 authentication and encryption standards protect sensitive information during these operations.
- Interface experts prioritize responsive layouts and intuitive navigation paths
- Systems architects optimize query speeds and error handling mechanisms
- Collaboration tools like Swagger documentation bridge communication gaps between teams
Consider an e-commerce platform: frontend code displays product images attractively, while backend logic calculates real-time inventory levels. Both layers must synchronize perfectly during checkout processes to prevent overselling or payment errors.
Technical leaders should assess team competencies in both areas when planning projects. Allocating resources effectively requires understanding how design choices impact server loads and how data structures influence interface responsiveness.
Exploring Backend App Development Strategies
Building robust digital platforms requires choosing between flexibility and speed. Technical teams often face a pivotal decision: invest in tailored systems or leverage pre-built solutions. This choice shapes scalability, maintenance costs, and time-to-market for new features.
Custom Backend vs. MBaaS Approaches
Tailored systems give complete control over data flows and security protocols. Enterprises handling sensitive transactions or unique workflows often prefer this route. For example, financial institutions might build proprietary fraud detection algorithms that third-party tools can’t replicate.
Mobile Backend as a Service (MBaaS) platforms like Firebase offer instant access to authentication and analytics tools. These services reduce coding efforts by 40-60% compared to custom builds. Startups launching minimum viable products frequently adopt this model to validate ideas quickly.
Cost, Speed, and Scalability Considerations
Initial investments differ sharply between approaches. MBaaS solutions operate on pay-as-you-go models, while custom builds require upfront infrastructure costs. However, long-term expenses often flip—subscription fees accumulate, whereas owned systems stabilize after deployment.
| Factor | MBaaS | Custom |
|---|---|---|
| Setup Time | Days | Weeks/Months |
| Ongoing Costs | Variable | Predictable |
| Feature Limits | Platform-dependent | None |
Scalability demands influence strategy selection. While MBaaS handles moderate growth effortlessly, complex applications might outgrow provider constraints. Custom architectures allow horizontal scaling across servers and regions without third-party bottlenecks.
Mobile App Functionality Driven by Backend Services
Modern platforms thrive on instant interactions that keep audiences engaged. Hidden systems orchestrate these experiences through precise coordination of data flows and user preferences. Technical teams must balance responsiveness with restraint to maintain positive engagement.
Enabling Push Notifications and Real-Time Features
Timely alerts transform passive users into active participants. However, excessive messages trigger frustration. Sophisticated systems analyze behavior patterns to deliver updates when they matter most. A fitness tracker might nudge users after inactive periods, while a news platform sends breaking alerts based on reading history.
Real-time synchronization powers collaborative tools and live updates. Stock trading platforms rely on millisecond-level price changes, while ride-sharing services track driver locations precisely. These features demand infrastructure that processes thousands of concurrent data streams without delays.
| Notification Strategy | Basic Approach | Optimized Method |
|---|---|---|
| Timing | Fixed schedules | Behavior-based triggers |
| Personalization | Generic messages | User-selected categories |
| User Control | All-or-none settings | Granular preference options |
Offline functionality ensures seamless experiences during connectivity gaps. Systems cache recent activity and sync changes once networks restore. This prevents workflow interruptions in productivity tools or navigation apps.
Effective implementation requires monitoring engagement metrics like open rates and session duration. Teams refine strategies using A/B testing to identify optimal message frequency and content formats. “The best notifications feel helpful, not intrusive,” observes a Meta product lead.
Technical Architecture Behind Backend App Development
Modern systems rely on invisible frameworks that act as glue between components. These structures manage communication, streamline workflows, and maintain stability under pressure. Technical leaders must prioritize architectures that balance flexibility with strict operational standards.
Understanding Middleware and API Integration
Middleware operates like a traffic controller for digital platforms. It routes requests between interfaces and databases while enforcing security rules. For example, when a user logs in, middleware verifies credentials before granting access to sensitive data.
APIs standardize how different software components interact. RESTful interfaces enable payment gateways to communicate with inventory systems seamlessly. “Well-designed APIs turn chaotic data exchanges into orderly conversations,” explains a Microsoft Azure architect. Proper version control prevents updates from breaking existing integrations.
Containerization and Virtualization Techniques
Containers package software with everything it needs to run consistently. Docker isolates applications from underlying infrastructure, simplifying deployment across environments. This prevents “works on my machine” conflicts during testing phases.
Virtualization maximizes hardware efficiency by splitting physical servers into multiple virtual machines. VMware solutions let teams run legacy systems alongside modern platforms securely. Both approaches improve scalability—containers handle sudden workload spikes, while virtualization optimizes resource allocation.
| Technique | Strengths | Use Cases |
|---|---|---|
| Containerization | Portability, rapid scaling | Microservices, cloud-native apps |
| Virtualization | Hardware optimization, isolation | Legacy system migration, multi-OS testing |
Orchestration tools like Kubernetes automate container management, ensuring high availability. Combined with robust API strategies, these methods create architectures ready for evolving business needs.
Best Practices for Secure and Scalable Backend Systems
Protecting digital infrastructure demands proactive strategies that evolve with emerging threats. Technical teams must balance rigorous safeguards with efficient resource allocation to maintain user trust and system responsiveness.
Implementing Robust Security Measures
Multi-layered authentication protocols prevent unauthorized access, combining biometric checks with time-based one-time passwords. Encryption standards like AES-256 secure data both at rest and during transmission. Regular penetration testing identifies vulnerabilities before attackers exploit them.
Third-party integrations require strict vetting to ensure compliance with organizational policies. Zero-trust architectures minimize breach risks by verifying every access request, regardless of origin. Automated alerts notify teams of suspicious activity patterns in real time.
Performance Optimization and Maintenance
Efficient caching mechanisms reduce server load during traffic surges while maintaining sub-second response times. Load balancing distributes requests evenly across servers, preventing bottlenecks during peak usage periods.
Scheduled audits streamline database management by removing redundant entries and optimizing queries. Monitoring tools like New Relic provide actionable insights into latency issues or memory leaks. Proactive updates ensure compatibility with evolving security frameworks and hardware advancements.